Using the Windows Active Directory within ScaleArc allows for automatic synchronization of Windows AD user authentication credentials from the AD domain to ScaleArc. These synchronized credentials can then be configured for database user Authentication Offload in the ScaleArc cluster configuration.
You can implement Windows AD in one of two ways:
Review the following prerequisites for RODC configuration before you begin configuring Windows AD.
Prerequisites
Before joining the domain you should have completed the following steps on ScaleArc and the AD and DNS of the domain:
Make sure you have ScaleArc, version 3.11.x installed and running for this configuration.
- ScaleArc recommends you configure the AD DC server as the NTP server in the ScaleArc configuration. The timezones on both the AD DC server and ScaleArc HA pair should also be the same. It is acceptable for the DC and ScaleArc to use the same NTP server, but essential that they be in time synchronization for Windows Authentication to work properly.
- Ensure that the Windows AD domain has been prepped to allow Read-Only Domain Controller (RODC) support. If you have not run adprep /rodcprep on your forest to allow RODCs to join your domains, run it once for your forest before you attempt to have ScaleArc join a domain in your forest.
- Make sure you have observed the maximum length for a hostname recommended by Microsoft for the ScaleArc hostname.
- Verify the primary DNS setting on ScaleArc is correct and ScaleArc is able to ping the AD server by hostname. ScaleArc's primary DNS server should in most cases be the AD DC server; this is the usual setup in AD. If it is not, ScaleArc and the AD domain should use the same DNS server.
- Ensure that DNS forward and reverse lookup are configured correctly for the AD domain and the AD DC on the DNS server that ScaleArc uses.
Optionally, ensure that the Windows AD users who require access to databases serviced by ScaleArc are configured on the desired SQL Server instances. Users can be added to AD and SQL Server after this domain join procedure is complete, and will automatically appear as the user fetch cycle runs; however, pre-configuring some users will allow immediate testing of the ScaleArc AD Integration functionality.
Configure for RODC
Before you begin, review these best practices. Then, configure as follows:
- Click the Settings tab > System Settings on the ScaleArc dashboard.
- Click the Windows AD Setup tab. Select the RODC radio button.
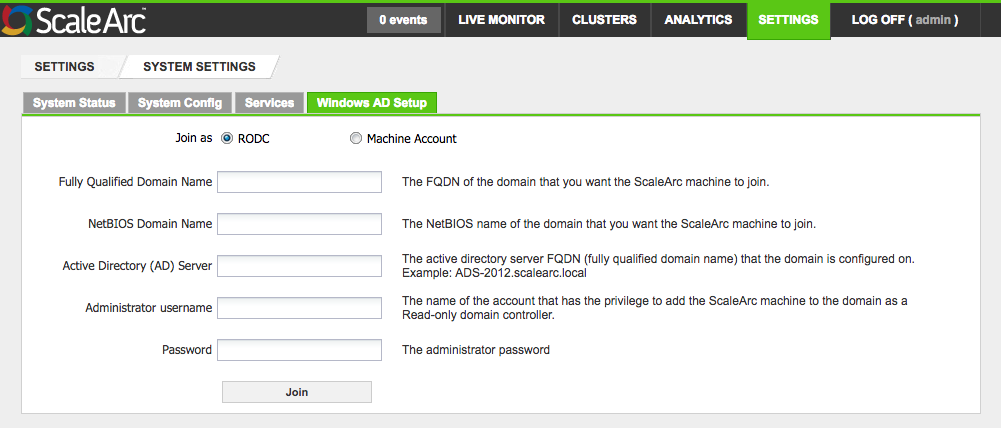
Complete the fields as follows.
Field Description Default/User input Fully Qualified Domain Name (FQDN) Enter the FQDN of the domain that you want the ScaleArc appliance to join.
Enter an appropriate domain name. NetBIOS Domain Name The NetBIOS name of the domain that you want the ScaleArc appliance to join. This is the "short" domain name, and is usually entered correctly by ScaleArc automatically.
Enter a NetBIOS name, if necessary. Active Directory (AD) Server
The AD DC server FQDN (fully qualified domain name) that the domain is configured on. Note that the server name should not include a trailing dot (".") at the end, unless you are using a valid DNS entry for the name. Enter the FQDN. Administrative username The username of the account that has the privilege to add the ScaleArc appliance to the domain as a Read-only domain controller.
Enter the username. Password The administrator password.
Enter the password. - Click Join the AD Domain to complete the set up. Once connected, you can use Unjoin the AD Domain to leave the domain.
- Add the appropriate domain users and/or groups to the Password Replication Policy for each of the ScaleArc RODC server objects in AD. Note that in an HA configuration this must be done in AD for both ScaleArc RODC objects for the HA pair, or users will not be allowed access after an HA failover operation.
- Add all desired users and groups into the Allowed RODC Password Replication Group.
- The Denied RODC Password Replication Group takes precedence, so membership in this group, or any group that is a member of this group, will prevent the user account from working with ScaleArc AD Integration even if it is allowed by membership in the Allow group. By default this Deny group contains all the usual administrator groups and administrative users in the domain.
- For further information on how to set user replication privileges for the ScaleArc RODC please refer to this KB article. - On the SQL Server instances that ScaleArc will communicate with, add either user accounts or group accounts to Security > Logins for those users who will access the servers through ScaleArc.
- In ScaleArc, go to Clusters > Settings > User &DBs.
- Click on the Fetch Users button. By default Auto Fetch Database Users is OFF. See Auto Fetch for details.
- Turn Auto Fetch Database Users ON. The default for the automatic synchronization interval is 60 seconds. Adjust this value, if required.
- User accounts that are enabled for RODC replication, and for SQL Server instance access, should appear at latest after two auto fetch intervals.
- There is no need to add the users from the Fetch Users dialog; if they are in the proper groups in AD, and have SQL Server access, they will be permitted to access ScaleArc and the SQL Servers.
- Note that if users are added from the Fetch Users dialog rather than being allowed by AD Integration, those users and their passwords will be "frozen;" the password in ScaleArc cannot be updated since it is no longer checked in the RODC, but is stored in the ScaleArc configuration files. The option to do this is to support legacy accounts. To put this another way, any user that appears in the Users & DBs dialog overrides the AD Integration feature and will not be eligible for AD Integration. To update the password for such a user, use the gear icon next to the user account in Users & DBs, not the account in the Fetch Users dialog.
- This also applies, as noted above in the Prerequisites, to pre-existing user accounts in Users & DBs. Such accounts should be deleted from the Users & DBs dialog prior to joining the domain, if AD Integration is desired for them.
- Note finally that for ScaleArc's monitoring to work properly, the first account in Users & DBs is not eligible for use with AD Integration. This is the cluster service account, used for health checks and configuration updates.

2017-02-16 01:17
The statement, "Before configuring HA, configure Active Directory exactly the same on both ScaleArc machines and then add them in HA. You can also configure HA and then join AD from the primary ScaleArc box. Refer to the High Availability section for more information on configuring HA in ScaleArc. "
still indicates that separate domain join then HA linkup is preferred; it is not. HA linkup should be accomplished before joining the domain and this is the preferred method; it is also possible to join each ScaleArc to the domain first, but all the domain join parameters must be identical or the HA linkup will be impossible. Also the information on the benefits of doing it this way have been left out of this section, but placed in the HA set up instructions; these benefits should be listed both places.
2017-08-07 03:48
topkv52f3h viagra for sale online - online viagra - viagra online - <a href="http://viagraonlinetop2017.com"> order viagra online</a> - viagra online pharmacy
2017-08-09 04:54
topuq34l1o free trial male enhancement pills male enhancement pills at gnc <a href="http://bestmalesenhancementpills.com"> prolong male enhancement</a> http://bestmalesenhancementpills.com - natural male enhancement pills rock hard male enhancement
2017-02-16 06:26
The first Prerequisite lists 3.10 as the installed version. This should be adjusted to 3.11 for this documentation set.
2017-02-16 06:34
In the second Prerequisite, it should be noted that the AD DC server is the preferred NTP server to ensure time synchronization which is essential to Windows AD authentication; however it is sufficient to use the same NTP server for ScaleArc as the AD DC uses and this is an allowed configuration.
2017-02-16 06:35
In the fifth Prerequisite, add a note that in most AD domains, the DC is the DNS server; in this case it should also be the DNS server in ScaleArc. If it is not the DNS server for the domain, the same DNS server that the DC uses should be used for ScaleArc.
2017-02-16 06:37
The sixth Prerequisite,
may be deleted as this is listed in the instructions for joining the domain below, and it is not actually a prerequisite.
2017-02-16 06:40
In Step 3, in the second line of the table, "NetBIOS Domain Name," in the Description column, note that this is ordinarily the short domain name of the FQDN of the domain, and is automatically set by ScaleArc. Also add the text, "if necessary," to the Default/User Input column.
2017-02-16 06:43
In Step 3, in the third line of the table, "Active Directory (AD) Server," in the Description column, instead of "active directory server" write "AD DC server."
2017-02-16 06:45
In #5, add the text, "Please note that the RODC Denied Password Replication Group policy has the highest precedence and overrides all allow settings. Users that will be used with ScaleArc must not be present in or a member of any group present in the RODC Denied Password Replication Group."
2017-02-16 06:46
In #8 note that more than one replication iteration may be necessary to fetch all users.
2017-02-18 02:41
CSS For Bill Bishop:
The text you have edited in the stepped instructions don't match the instructions in the comments section. Let's connect at 2.30 pm today (Friday) to go over them. Thanks, Meera